- Open a command line (Run > Type "cmd")
- Goto the java maven project folder. (Where the "pom.xml" is located)
- Type "mvn sonar:sonar" and hit enter. (Maven will start analyzing the project)
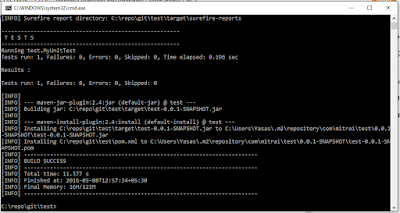
("Build Success" message at the end of analysis confirms the analysis has completed successfully)
You should now be able to see your java project in the SonarQube dashboard.
Analyzing Unit Test Results/Code Coverage for JAVA Maven Projects
(Please note that you must include a set of plugins in your pom.xml to analyze the code coverage.
E.g : "junit", "maven-surefire-plugin", "sonar-jacoco-listeners")
If you do not have the "junit", "maven-surefire-plugin", "sonar-jacoco-listeners" plugins in your pom.xml, simply copy and paste the same plugins from the following pom.xml.
pom.xml
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelVersion>4.0.0</modelVersion>
<groupId>com.mitrai</groupId>
<artifactId>test</artifactId>
<version>0.0.1-SNAPSHOT</version>
<name>Java :: Mitrai-TestProject :: UT Coverage with JaCoCo</name>
<properties>
<project.build.sourceEncoding>UTF-8</project.build.sourceEncoding>
</properties>
<dependencies>
<dependency>
<groupId>junit</groupId>
<artifactId>junit</artifactId>
<!-- Minimal supported version is 4.7 -->
<version>4.11</version>
<scope>test</scope>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-compiler-plugin</artifactId>
<version>3.3</version>
<configuration>
<source>1.5</source>
<target>1.5</target>
</configuration>
</plugin>
</plugins>
</build>
<!-- BEGIN: Specific to mapping unit tests and covered code -->
<profiles>
<profile>
<id>coverage-per-test</id>
<build>
<plugins>
<plugin>
<groupId>org.apache.maven.plugins</groupId>
<artifactId>maven-surefire-plugin</artifactId>
<!-- Minimal supported version is 2.4 -->
<version>2.13</version>
<configuration>
<properties>
<property>
<name>listener</name>
<value>org.sonar.java.jacoco.JUnitListener</value>
</property>
</properties>
</configuration>
</plugin>
</plugins>
</build>
<dependencies>
<dependency>
<groupId>org.sonarsource.java</groupId>
<artifactId>sonar-jacoco-listeners</artifactId>
<version>3.8</version>
<scope>test</scope>
</dependency>
</dependencies>
</profile>
</profiles>
<!-- END: Specific to mapping unit tests and covered code -->
</project>
Also note that having the above plugins will analyze 0 unit tests, if you do not have any unit tests written in your code. (If you are using the test Java Maven project, you shall note there is one Unit test case while its being analyzed.)
- Open a command line (Run > Type "cmd")
- Goto the java maven project folder. (Where the "pom.xml" is located)
- Type "mvn clean org.jacoco:jacoco-maven-plugin:prepare-agent install" and hit enter. (Maven will Prepare jacoco agent to allow coverage report generation, build the project, and execute the unit tests)
- Type "mvn sonar:sonar" and hit enter. (Maven will start analyzing the project along with the unit test results created from the previous step and publish results in SonarQube dashboard)
SonarQube dashboard should now consist your java project's analysis results along with the the unit test results / code coverage.