The whole shebang on Cryptography
This will be the first part of a series of posts on Cryptography /SSL Certificates / IPSec /SSH and will cover the useful facts/tools/commands as well.
How everything starts ... :)
Me : Shall we have pizza for lunch?
Tommy : Oh yeah, lets order online. Shall we use your card?
Me :(I'm afraid to expose my credit card information to an online pizza website)
What is Cryptography?
Cryptography is a method of storing and transmitting data in a particular form so that only those for whom it is intended can read and process it.
Var
|
Description(PlainText)
|
m
|
Message (Plain-text)
|
c
|
Cipher-text
|
E
|
Encryption Algorithm
|
D
|
Decryption Algorithm
|
ke
|
Encryption Key
|
kd
|
Decryption Key
|
1| Symmetric Key Cryptography /Private Key Encryption
- Same key is used to encrypt data as well as to decrypt data.
- : Everyone shares same secret key. (k = ke = kd)
- Faster than Asymmetric key/Public key Encryption.
*| Message Authenticity and Integrity - Message Authentication Code (MAC)
Message Authentication Code (MAC) is a short piece of information used to confirm that the message came from the stated sender (its authenticity) and has not been changed.
- A MAC requires two inputs: a message and a secret key known only to the originator of the message and its intended recipient(s).
- This allows the recipient of the message to verify the integrity of the message and authenticate that the message's sender has the shared secret key.
- If a sender doesn’t know the secret key, the hash value would then be different, which would tell the recipient that the message was not from the original sender.
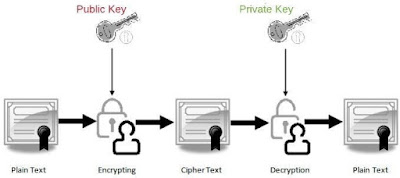
2| Asymmetric key Cryptography /Public key Encryption
- Two keys are used in the process (public key and private key)
- : Only one party has the secret key. ( ke != kd)
- Slower when compared to Symetric Key Encription.
Like a lot of things in computing, it comes to a trade off between performance and computing when you have to decide whether to use Symmetric key encryption or asymmetric key encryption .- Wait ... Encryption is NOT All !!!

*| Message Authenticity and Integrity - Digital signature
Digital signature is a mechanism by which a message is authenticated proving that a message is coming from a given sender.
E.g : Much like a signature on a paper document.
Suppose that Rose wants to digitally sign a message to Jack. To do so,
- she uses her private-key to encrypt the message;
- she then sends the message along with her public-key (typically, the public key is attached to the signed message).
Key Types, Key Sizes and Algorithms used to generate Keys
Public key
- A large numerical value that is used to encrypt data.
- The key can be generated by a software program, but more often, it is provided by a trusted, designated authority.
- Made available to everyone through a publicly accessible repository or directory.
Public key
- A large numerical value that is used to encrypt data.
- The key can be generated by a software program, but more often, it is provided by a trusted, designated authority.
- Made available to everyone through a publicly accessible repository or directory.
Private Key
- Another large numerical value that is mathematically linked to the public key.
- In asymmetric cryptography, whatever is encrypted with a public key may only be decrypted by its corresponding private key and vice versa.
Algorithms
RSA and DSA are two of the algorithms which are used to encrypt public/private keys in cryptography.
- RSA - (Rivest, Shamir, & Adleman public key encryption technology)
- DSA - (Digital Signature Algorithm)
Key Sizes
The key size (bit-length) of a public and private key pair decides how easily the key can be exploited with a brute force attack.
The more computing power increases year after year, it requires more strong keys to secure transmitting data.
- There is no requirement for the key length to match the block size in any way;
- However, cryptographers are in love with binary, so key length will usually be a power of 2 like 128 or 256, and so will block size be.
The more computing power increases year after year, it requires more strong keys to secure transmitting data.
- RSA claims that 1024-bit keys are likely to become crack-able some time between 2006 and 2010 and that 2048-bit keys are sufficient until 2030.
- An RSA key length of 3072 bits should be used if security is required beyond 2030.
For Advanced Learners
Public Key Encryption and Digital Signature:How do they work?
If you want to learn about SSL certificates > Part 2 - The whole shebang on SSL Certificates
If you want to learn about IPSec > Part 3 - The whole shebang on IPSec
If you want to learn about SSH > Part 4 - The whole shebang on SSH
If you want to learn about SSL certificates > Part 2 - The whole shebang on SSL Certificates
If you want to learn about IPSec > Part 3 - The whole shebang on IPSec
If you want to learn about SSH > Part 4 - The whole shebang on SSH